API keys are small strings with outsized blast radius. Once exposed, they can let an attacker impersonate systems, drain credits, or pull sensitive data. In 2024, researchers reported millions of leaked secrets on public GitHub alone, a reminder that the weakest link is often how a secret is shared or stored after it is issued. The safest way to share an API key is not a particular chat app or email client, it is a short, auditable workflow that keeps the key encrypted end to end, limits how long it exists in transit, and leaves no retrievable copy behind.
This guide shows a practical, security-first way to hand off an API key with near zero trace, then harden your process for teams. It also explains why ephemeral, client-side encrypted links are the right tool for the job.
Why sharing an API key is risky by default
Common channels create persistent, searchable copies of secrets:
- Email, inboxes retain messages for years, get forwarded, and are often indexed by corporate search and eDiscovery.
- Chat, threads and attachments are searchable, previews can leak content, and admins or exports can reveal history. See our guide on why Slack and Teams are risky for credentials, it applies to API keys too. Why Slack and Microsoft Teams Are Not Safe for Passwords
- Tickets and docs, durable records designed for collaboration, not secrecy.
- Screenshots and PDFs, copied and synced across devices and backups.
Once a copy exists in any of these systems, you must treat it like a long-term exposure. This runs counter to guidance from the security community, for example the OWASP Secrets Management Cheat Sheet, which advises against storing secrets in code, logs, tickets, or shared docs and recommends limiting lifetime and access wherever possible. OWASP Secrets Management Cheat Sheet
What "safest" looks like, principles to follow
- End-to-end, zero-knowledge encryption, the provider cannot read the secret, encryption happens locally in the browser or client.
- One-time access, the link or envelope burns after a single view.
- No content stored server side, no plaintext or decryptable payload kept by the service.
- Short window of exposure, share just in time and rotate shortly after delivery.
- Recipient verification, confirm the intended person accessed it.
- Minimal metadata with useful audit, enough event detail to prove access for compliance without retaining the secret itself.
NIST's key management guidance highlights limiting key exposure, scoping, and rotation as core controls. These controls matter as much during handoff as during steady state. NIST SP 800-57 Part 1
The safest way to share an API key, a step-by-step workflow
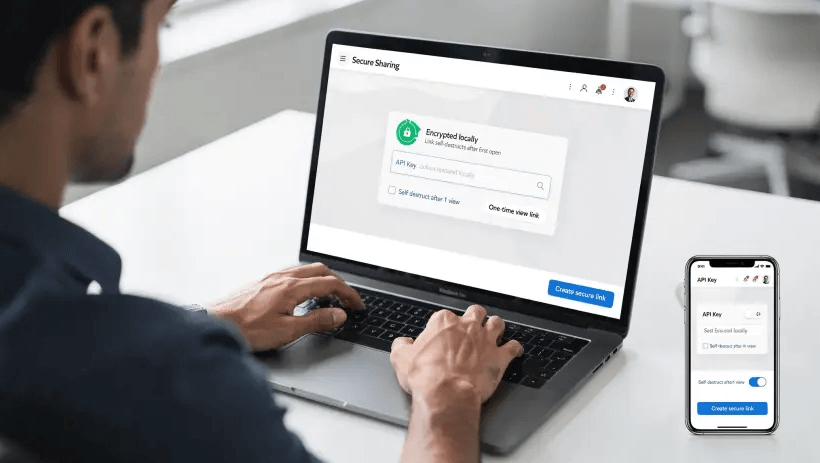
The following procedure uses Nurbak, a zero-knowledge tool for self-destructing links that encrypts secrets locally with AES-256 and leaves no retrievable copy on the server. You can adapt these steps to your team's tools, but the security properties are the same.

Before you share
- Generate a fresh, scoped key, restrict permissions to the minimum, set IP allow lists or environment-level access if the platform supports it.
- Plan a rotation, decide when you will rotate or revoke after the recipient confirms receipt.
- Avoid intermediate copies, do not paste the key into tickets or notes.
Create a one-time, zero-knowledge link
- Go to Nurbak, paste the API key, and create a self-destructing, one-time access link. Encryption happens locally, the service uses AES-256 under a zero-knowledge design and does not store or log secret content.
- Copy the generated link. At this point, the ciphertext is the only thing that ever leaves your device.
Deliver over separate channels
- Send the one-time link in your normal channel, for example Slack or email. The content is still protected because it can only be opened once and is encrypted end to end.
- Send a short verification code or phrase out of band, for example a 6 word sentence over SMS or a brief voice call. The recipient replies with the phrase after opening the link. This gives you simple sender-receiver verification without passwords in the tool.
Recipient actions
- Open the link once, decrypt locally, and store the key in an approved secrets manager or deployment system. Do not keep it in notes or chat.
- Test the key immediately in the intended environment.
Example test, replace with your API's scheme:
curl -H "Authorization: Bearer <api_key>" https://api.example.com/v1/pingAfter delivery
- Confirm the link is burned, Nurbak links self-destruct after one read, and use audit access logs to confirm that the link was accessed.
- Rotate on schedule if the platform supports fast rotation, and always revoke old keys once the handoff is complete.
- Record the event in your change log without the secret, date, recipient, issuer, and the key scope.
Why this workflow works
- It separates the message from the secret, your chat or email history only contains a dead link, not the key.
- It minimizes lifetime, the key exists in transit for minutes rather than days.
- It keeps plaintext out of third party servers, a zero-knowledge architecture makes provider access mathematically implausible.
- It maintains accountability, audit access logs give teams proof that the link was opened without persisting the secret.
Channels compared, how risky are common options
| Sharing method | Risk level | Why it is risky or safe | How to make it safer |
|---|---|---|---|
| Raw key in email | High | Persistent storage, forwards and mailbox exports | Do not use for secrets |
| Raw key in chat | High | Searchable history, previews, admin access | Do not use for secrets, use ephemeral links instead |
| Ticketing system | High | Indexed and long lived by design | Do not store secrets, reference a burned link |
| Password manager "send" feature | Medium | Usually encrypted, may create retrievable items | Use one-time views when supported, delete promptly |
| Self-hosted paste with client-side encryption | Medium | Secure if configured, operational overhead | Restrict access, ensure true client-side encryption |
| Nurbak one-time link | Low | Client-side AES-256 encryption, zero-knowledge, self-destruct after read | Verify recipient out of band and rotate after delivery |
For a deeper look at why persistent collaboration tools are a poor fit for secrets, see our analysis of Slack and Teams. Why Slack and Microsoft Teams Are Not Safe for Passwords
Team playbook, make it a repeatable SOP
- Scope first, issue keys with the least privilege needed and environment limits.
- Share via one-time, zero-knowledge links only, do not paste keys into tickets.
- Verify recipient, use a second channel to confirm the person and the one-time access event.
- Store in a secrets manager, require recipients to put keys in approved vaults or environment stores immediately.
- Rotate promptly, schedule rotation and revoke old keys.
- Keep an audit trail without content, record who issued, who received, and when the key was rotated. Nurbak provides audit access logs to support this requirement.
This workflow aligns with compliance expectations in SOC 2 and ISO 27001, which emphasize least privilege, access control, and traceability. For guidance on meeting these standards while sharing credentials, read our practical overview. SOC2 and Password Sharing: How to Maintain Compliance in Remote Teams
Additional hardening tips for developers
- Prefer short-lived tokens when your platform supports them, rotate API keys more often than passwords.
- Restrict by context, use IP allow lists, service accounts, and environment segmentation.
- Enable secret scanning, turn on repository secret scanning and CI checks to block accidental commits. GitHub secret scanning
- Monitor for exposure, third party reports show secrets frequently leak to public repos and registries. GitGuardian State of Secrets Sprawl 2024
- Avoid transitive exposure, never include keys in crash logs, analytics, or demo datasets.
Why choose Nurbak for API key handoffs
Nurbak is purpose-built to share sensitive information with no trace. Secrets are encrypted locally using AES-256, links are one time, and the architecture is zero knowledge by design. The service does not store or log secret content. Teams can use audit access logs, an admin dashboard with analytics, and integrations that fit existing infrastructure, which helps satisfy internal security and external regulatory requirements.
In short, you get the privacy of a sealed envelope, with the visibility security teams need.
Frequently Asked Questions
Is sending a one-time link in Slack or email safe? Yes, when the content is end-to-end encrypted, one time, and zero knowledge, the channel only carries a dead link after it is opened. Avoid posting plaintext keys directly.
Do I need to add a password to the link? With true client-side encryption and one-time access, an additional password is often unnecessary. If you add one, share it out of band.
What should the recipient do after opening the link? Store the key in an approved secrets manager or deployment system, test it, then remove any local copies such as clipboard managers or notes.
How soon should I rotate the API key? Ideally schedule rotation immediately after confirmation of receipt or after initial use. Use the shortest practical lifetime your platform allows.
What if the link is intercepted? A zero-knowledge, one-time link reveals nothing until opened, and it burns after a single view. Verify the recipient and rotate if you suspect interception.
Is base64 encoding or splitting the key across messages helpful? No, base64 is not encryption and message splitting creates more places to leak. Use proper encryption and one-time delivery.
How do I prove compliance without storing secrets? Keep event records, who issued and who accessed, and rely on tools that provide audit access logs without storing secret content.
Ready to share an API key without leaving a trace, generate a one-time, zero-knowledge link with Nurbak in seconds. Start here, Nurbak, Share secrets, leave no trace.
References and further reading
- OWASP Secrets Management Cheat Sheet, guidance on handling secrets safely. OWASP
- Verizon Data Breach Investigations Report 2024, credentials remain a top vector. Verizon DBIR
- GitGuardian State of Secrets Sprawl 2024, prevalence of leaked secrets in public repos. GitGuardian

