It is easy to treat data security and data privacy as separate checklists. Security keeps data confidential, integral, and available, while privacy constrains what you collect, why you collect it, and how long you keep it. In practice they succeed or fail together. Misaligned policies lead to contradictory requirements, unnecessary data retention, and recurring audit findings. This guide shows how to align your policies so security controls directly support privacy outcomes, with concrete steps you can complete this quarter.
What policy alignment really means in 2025
Alignment is not about copying text between documents. It means your control set, evidence, and operations map cleanly to both security and privacy objectives. Modern frameworks already point in this direction. The updated NIST Cybersecurity Framework 2.0 and the NIST Privacy Framework explicitly encourage crosswalks between security functions and privacy outcomes. ISO took a similar path by pairing 27001 with the privacy extension 27701, see ISO/IEC 27701 overview. Foundational legal principles like GDPR Article 5, including data minimization and storage limitation, make the linkage concrete, see GDPR Article 5 principles.
When your security controls reinforce those privacy principles, you gain fewer incidents, fewer exceptions to manage, and faster third party risk reviews. When they do not, you inherit a backlog of compensating controls and manual cleanup work.
Five collisions between security and privacy to fix first
These are the recurring places where separate teams unintentionally work against each other:
- Retention versus logging, privacy says keep data only as long as necessary, while security keeps verbose logs for long periods. Solve with tiered retention and redaction by default.
- Backups versus the right to erasure, deletion requests fail if older backups still carry personal data. Solve with short backup lifecycles for systems that store PII and documented restore filters.
- Ticketing and chat versus data minimization, screenshots and copy paste push secrets and PII into long lived systems. Solve with templates that block sensitive fields and ephemeral channels for secrets.
- Vendor monitoring versus purpose limitation, aggressive telemetry or session recording can exceed stated purposes. Solve with scoped telemetry and clear notices.
- Secrets handling versus confidentiality, password sharing over email or chat violates both security and privacy doctrines. Solve with one time, client side encrypted delivery and immediate destruction after use.
If you address these five, you remove the bulk of daily friction and reduce the probability of conflict between your security and privacy policies.
An alignment blueprint, privacy principles mapped to security controls
The table below shows how to express privacy requirements as specific security controls, policy language, and auditable evidence.
| Privacy principle | Security control alignment | Policy language example | Evidence |
|---|---|---|---|
| Data minimization | Collection reviews, input validation to block secrets in tickets, ephemeral channels for sensitive values | Collect only necessary personal data. Secrets and credentials must never be sent by email or chat, they must be transmitted via one time, client side encrypted links. | Data inventory, ticket templates, approved tools list, training records |
| Storage limitation | Short retention defaults, automated deletion, ephemeral transfer for secrets, backup lifecycle limits | Production data and logs follow documented retention schedules. Secrets have a standard retention of zero days, they are destroyed on first access. Backups of systems with PII have time bound lifecycles. | Retention policy, TTL settings, deletion job configs, backup lifecycle SOPs |
| Integrity and confidentiality | Encryption in transit and at rest, authenticated encryption for sensitive data, client side encryption for secrets | All personal data is encrypted in transit and at rest. Highly sensitive secrets are protected with AES 256 authenticated encryption, and for transmission we use zero knowledge tools. | Encryption settings, key management procedures, vendor security pages, internal verification, see AES 256 explained |
| Purpose limitation | Role based access control, least privilege scopes on tokens and API keys, segregation of duties | Access to personal data is granted only for documented purposes. API keys and tokens must be scoped to the minimum permissions needed for the task. | Access reviews, token scope definitions, change tickets |
| Transparency and access rights | Discoverability of data, DSAR workflow, redaction tooling | We maintain an index of where personal data resides and can respond to access and deletion requests within stated timelines. | DSAR tracker, data map, deletion workflow evidence |
| Accountability and auditability | Event logging that captures access events without storing content, tamper evident logs | Systems log who accessed what and when, not the data itself. Secret exchange records capture access events only. | Log samples, SOC reports, secret access audit entries |
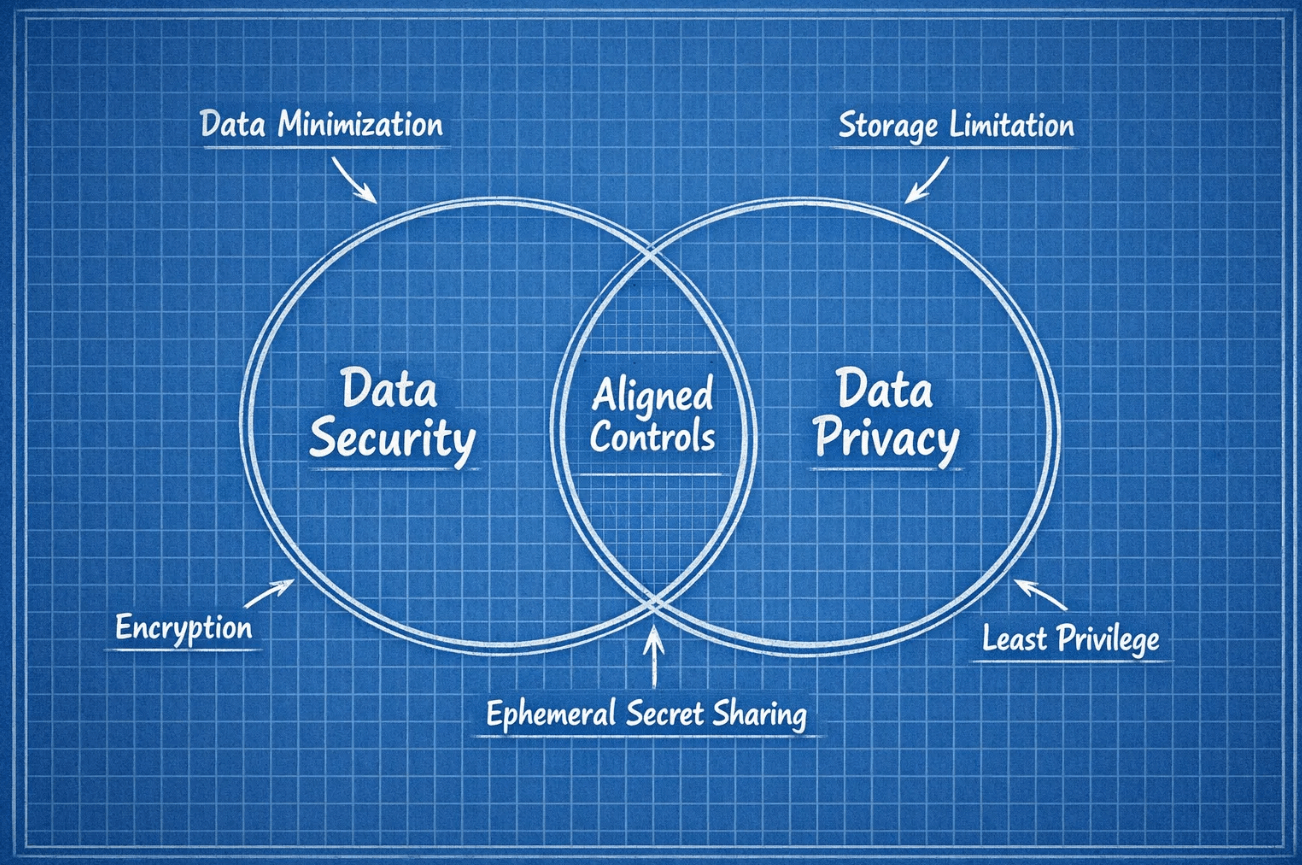
Build one control catalog, many outcomes
Create a single internal catalog of controls and map each item to both security and privacy requirements. For example, your encryption control can reference NIST CSF and ISO 27001 on the security side, and GDPR Article 5.1(f) on the privacy side. The outcome is one owner, one set of procedures, and one place to store evidence for auditors. This removes duplicative wording and inconsistent interpretations across policies.
- Use a common taxonomy, label every control with a unique ID so it can be referenced in standards, policies, and SOPs.
- Tie controls to evidence, define the artifact you will produce for each control, such as configuration exports, redaction rules, or access reviews.
- Introduce exceptions only once, centralize risk acceptance so the same exception applies to both policies with the same review date and owner.
A 90 day plan to align data security and data privacy
Days 1 to 30, discover and deconflict
Document where personal data and secrets actually flow. Inventory intake forms, customer support tools, logs, backups, and collaboration channels. Compare what you do to what your policies say. Flag contradictions, like indefinite log retention in a system that stores PII, or a help desk that accepts passwords. Identify quick wins, such as disabling file uploads on support forms, shortening retention for verbose logs, and adding warnings to ticket templates that block secrets.
Days 31 to 60, rewrite policies to mandate controls
Replace ambiguous language with operational mandates. Require least privilege for tokens, short retention by default, and client side encrypted, one time delivery for secrets. Align wording with frameworks you already use, for example NIST CSF 2.0 and the NIST Privacy Framework. Publish companion SOPs that any engineer or analyst can follow without asking legal to translate policy prose.
Suggested policy insert for secrets transmission, Secrets and credentials must be transmitted using one time, client side encrypted links. The provider must operate on a zero knowledge basis, meaning the server cannot see the decryption key. Links expire after a single view or within 24 hours, whichever comes first.
Days 61 to 90, operationalize and prove
Roll out the approved tools, set technical guardrails, and train teams. Configure log retention and redaction, add guardrails in ticketing to block sensitive content, and adopt a standard tool for secrets exchange that produces event level audit entries without storing content. Prepare an evidence pack for auditors that shows the before and after state for key systems and links policy language to proof.
For deeper implementation guidance on secret exchange, see How to share a secret with one time links and SOC2 and password sharing in remote teams.
Case study pattern, a secrets transmission policy that serves both teams
Secrets are a perfect place to demonstrate alignment. Security wants confidentiality, integrity, and one time use. Privacy wants data minimization and storage limitation. You can satisfy both by adopting ephemeral, zero knowledge delivery.
What this looks like in practice:
- Create one time, self destructing links for credentials, API keys, recovery codes, and temporary admin passwords.
- Encrypt locally in the browser so only ciphertext reaches the server, and the decryption key stays in the URL fragment.
- Set the link to burn on read, so the data does not persist beyond the single intended access.
- Record access events without storing the secret, so you have auditability without retention of sensitive content.
Nurbak was built for this exact pattern. It uses AES 256 with a zero knowledge architecture, generates one time access links, and permanently deletes the secret after it is read. Admins can review audit access logs, while the service avoids storing or logging secret content. This helps teams meet storage limitation and confidentiality principles at the same time. Learn more in Client side vs server side encryption and our overview of GDPR compliant ephemeral sharing.
Metrics and evidence that prove alignment
Auditors and buyers want to see objective progress. Track a small set of measures that directly reflect policy outcomes.
| Objective | Metric | Target | Evidence artifact |
|---|---|---|---|
| Minimize sensitive data in collaboration tools | Percentage of tickets or chat messages containing secrets | Trend to near zero, sustained month over month | DLP matches, ticket template blocks, sampling report |
| Limit retention | Average retention days for verbose logs that may contain PII | Aligned to policy by system class, often 30 to 90 days | SIEM retention settings, lifecycle policies |
| Protect secrets in transit | Share of secrets delivered via one time, client side encrypted links | 100 percent for credentials and recovery codes | Tool audit access logs, SOP adoption checklist |
| Respond to deletion requests | Median time to honor erasure across primary systems | Within regulatory commitment | DSAR tracker and deletion job outputs |
| Reduce backup exposure | Percentage of systems with time bound backup lifecycles when PII is present | 100 percent of in scope systems | Backup policy, storage lifecycle configs |
| Control access | Timely completion of access reviews for systems containing personal data | 100 percent on schedule | Access review records and remediation tickets |
Governance and enablement
Assign a single owner per control and publish a RACI that covers policy writing, implementation, and evidence. Run short enablement sessions for support, engineering, and vendor management so teams know how to act on the policies they just received. Focus training on the workflows that create most incidents, ticketing practices, secret exchange, and log retention.
Anticipate two practical snags and plan for them:
- Link previews, some chat tools unfurl links through scanners that may consume one time links. Send context separately and follow your tool's guidance for avoiding previews.
- Shadow data, prevent sensitive fields in exports and screenshots from entering long lived systems.
Tooling that accelerates alignment
Use a small, well understood toolset rather than a sprawling stack. For secret transmission, adopt a zero knowledge, one time link tool so your collaboration systems carry only dead links and event records. For encryption, favor authenticated modes and verify settings. For governance, maintain a single control catalog that references both security and privacy frameworks.
If your team needs a fast path to aligned secret handling, you can start right now with Nurbak. It enables client side encrypted, self destructing links with zero knowledge security, no data logging or storage of secret content, audit access logs, and an admin dashboard that plugs into existing infrastructure. That combination gives both security and privacy teams the control and evidence they need without adding operational overhead.
Ready to make secret transmission compatible with both data security and data privacy policies, Create a zero knowledge one time link and add the policy insert above to your handbook today.

