
La mayoría de los incidentes de seguridad no son causados por fallos criptográficos exóticos, ocurren porque los datos sensibles dejan un rastro largo a través de buzones, registros de chat, sistemas de tickets y copias de seguridad. Si tu objetivo es el intercambio seguro de información, la reducción de riesgo más rápida es minimizar las huellas. Los enlaces de cero huella hacen que eso sea el predeterminado: cifrar localmente, entregar una vez y eliminar automáticamente para que no quede nada que encontrar.
Qué significa realmente cero huella
Zero-trace is a practical outcome, not a buzzword. It means the act of sharing leaves no recoverable copy of the secret on intermediate systems (providers, relays, or organizational archives). The approach aligns with data minimization and storage limitation principles in modern privacy law and security frameworks, where you only collect and retain what you strictly need and for as long as needed.
- Privacy by design, supported by GDPR principles such as data minimization and storage limitation. See Article 5 and Article 17 (Right to erasure) for formal grounding. For accessible summaries, review the GDPR data minimization principle and the Right to be forgotten.
- NIST emphasizes minimization and purpose limitation as foundational privacy safeguards. See the NIST Privacy Framework for controls that reduce retention and exposure.
- OWASP recommends keeping secrets out of communication channels and source control. The OWASP Secrets Management Cheat Sheet is a good operational reference for developers and IT.
In short, zero-trace links are a tool to implement minimization by default when humans need to hand off sensitive data.
Cómo funcionan los enlaces de cero huella (en lenguaje simple)
- You paste a secret into a secure page. Your browser encrypts it locally using strong primitives (for example, AES-256 in an authenticated mode).
- Only ciphertext goes to the server. The decryption key stays in the URL fragment so the server never sees it.
- You send a one-time link to the recipient. When they open it, their browser fetches the ciphertext, decrypts locally, and the link burns after first access or after a short TTL.
- Nothing readable remains on the server. With zero-knowledge architecture and self-destruction, the provider cannot read or recover the secret.
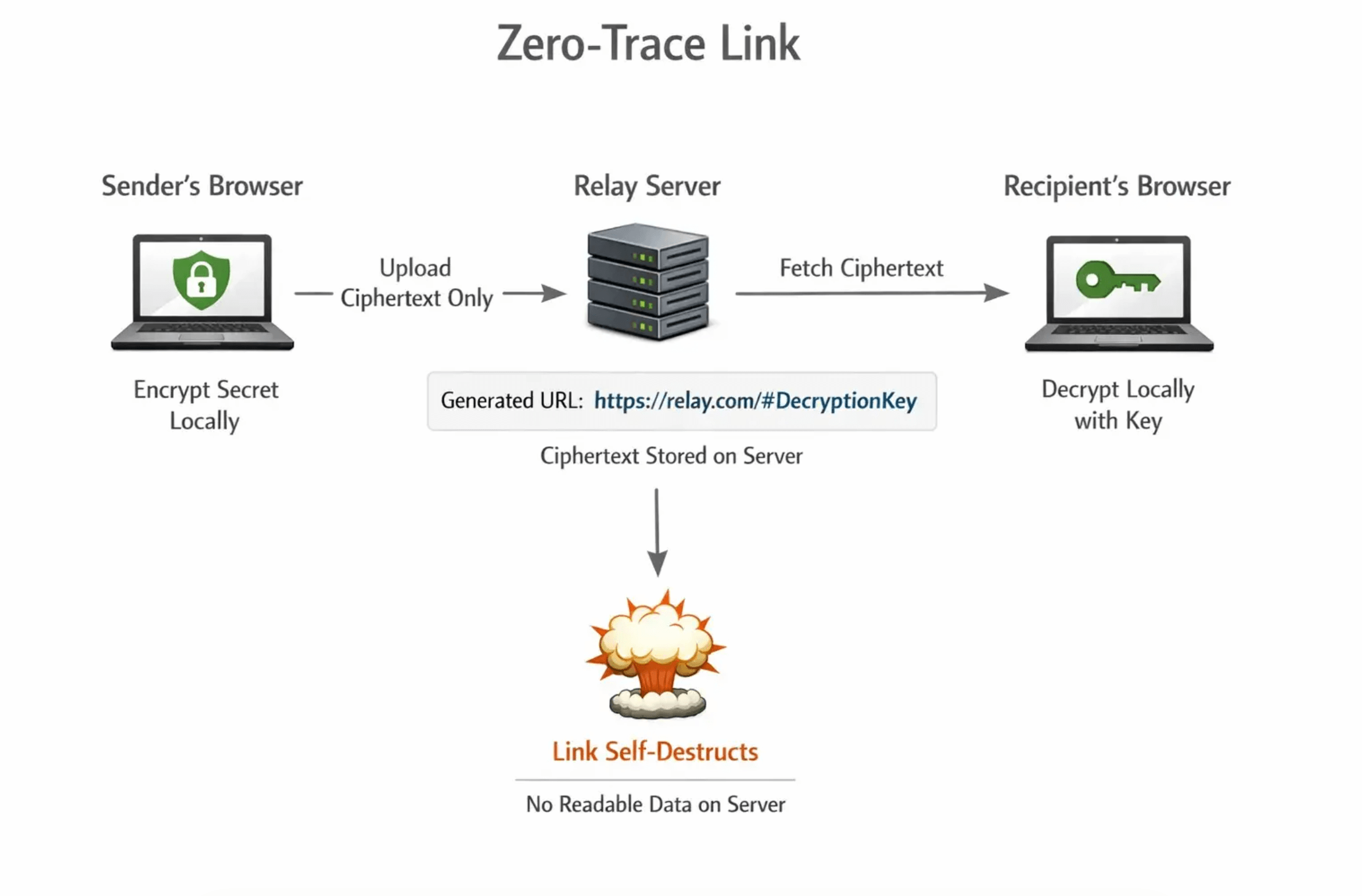
Por qué esto mejora el intercambio seguro de información
Traditional channels create durable copies you cannot reliably eradicate. Even after deletion, artifacts persist in search indexes, backups, and notifications. With zero-trace links, the default is the opposite: the window of exposure is small, the number of copies is minimal, and proof of access is available without storing content.
Here is a quick look at residual traces by channel:
| Channel | Copies created | Provider can read content | Searchable by admins | Link preview risk | Erasure difficulty |
|---|---|---|---|---|---|
| Many, across sender, recipient, gateways, backups | Often yes | Often yes | Medium | Hard | |
| Chat (Slack, Teams) | Many, chat history and exports | Often yes | Often yes | High | Hard |
| Ticketing (Jira, Zendesk) | Many, tickets and attachments | Often yes | Often yes | Low | Hard |
| Password manager sharing | Few, vault copy under org controls | No (if E2EE) | Admins may see metadata | Low | Medium |
| Zero-trace one-time link | One, short lived, then destroyed | No | Metadata only | Manageable with previews disabled | Easy |
Note: This table summarizes typical defaults. Your environment and settings matter.
For teams, the security upside shows up in fewer credential rotations, fewer policy exceptions during audits, and lower incident response workload. That is why industry reports repeatedly call out stolen credentials as a top breach vector. The annual Verizon Data Breach Investigations Report highlights this pattern consistently.
Una política de compartición de cero huella que puedes implementar en días
You do not need to rewrite your security stack. You just need to separate communication from secret transmission and set simple defaults.
- Define what is a secret: passwords, API keys, recovery codes, private SSH keys, card numbers, bank details, PII that could enable fraud.
- Map TTLs by data class. Short windows reduce risk and support privacy principles.
- Require one-time, client-side encrypted links for human-to-human handoffs.
- Deliver links in your normal channel, but never paste secrets directly.
- Verify recipient identity out of band for high risk operations, then burn after use and rotate credentials if needed.
Recommended TTLs and controls by sensitivity:
| Data class | Examples | Recommended TTL | Controls |
|---|---|---|---|
| Very high | Root creds, private keys, master API tokens | 5 to 15 minutes, one view | Out-of-band verification, IP notify, mandatory rotation after use |
| High | Admin passwords, database creds, recovery codes | 15 to 60 minutes, one view | Recipient acknowledgment, rotate upon task completion |
| Medium | Scoped API keys, temporary access links | Same day, one view or limited views | Scope and expiry on the key itself |
| Low | Non-sensitive notes that should still not persist | 24 hours, one view | Optional verification |
Adjust these defaults to match your risk appetite and regulatory context.
Mejores prácticas operativas, las partes que realmente previenen filtraciones
- Separate channels: talk in chat or email, transmit secrets via zero-trace links. This keeps your archives free of stored secrets.
- Disable link previews in gateways that fetch URLs automatically. If you cannot control the gateway, instruct users to send the link with preview suppression or as code text so bots do not open it.
- Verify recipients when it matters. A quick call or a second factor acknowledgement beats assumptions.
- Train for the last mile. Ask recipients to store the secret in an approved password manager, then delete clipboard history. Remind them that screenshots are forever.
- Keep the blast radius small. Prefer scoped, temporary credentials over long lived ones so a leak is less damaging.
- Monitor, do not over collect. Audit the fact that a link was accessed, without keeping the content.
Cuándo no usar enlaces de cero huella
If you require a durable, legally retained record of the content, for example signed contracts or regulated customer communications, you need a system of record with proper retention and access control. Zero-trace links are ideal for secrets and sensitive values that do not need to exist after handoff.
Cómo Nurbak implementa enlaces de cero huella
Nurbak is built to make the zero-trace pattern easy for everyone in your company, from IT to HR to Finance.
- Client-side, zero-knowledge encryption, secrets are encrypted in the browser using AES-256, only ciphertext is relayed.
- Self-destructing, one-time links, burn after reading or after a short TTL, so secrets disappear by default.
- No data logging or storage of secret content, the platform does not retain what you share.
- Audit access logs for accountability, teams can see access events without exposing contents.
- Admin dashboard and analytics, policy baselines, and visibility for security leaders.
- Integrates with existing infrastructure, suitable for multiple industries and compliance goals.
If you want a deeper technical dive on client-side encryption and threat models, read our guides on client-side vs server-side encryption and the practical steps in how to share a secret with one-time links.
Guías de departamentos que puedes adoptar hoy
- IT and Security: Temporary admin or root access for vendors, create isolated credentials, share via a one-time link, rotate as soon as the job is done. This eliminates zombie access.
- Engineering: API keys and environment variables for new services, share scoped keys that expire, transmit with a zero-trace link, and commit nothing to chat or git.
- HR: 2FA recovery codes for new hires, deliver once, instruct the employee to import into their password manager, burn the link, and mark complete in the onboarding checklist.
- Finance: One off bank details or card data, set a very short TTL, confirm by phone, and request immediate deletion after the transfer is completed.
- Legal and Sales: Diligence portals or redlines that include secrets, send the secret value via a one-time link, keep the negotiation in email, keep the secret out of the archive.
Medir el éxito, para que el hábito se mantenga
- Secret-in-chat metric: target zero secrets pasted in chat or tickets.
- Rotation workload: measure reductions in emergency credential rotations.
- Audit readiness: demonstrate that sensitive values are not retained in mailboxes or chat exports, supported by access-event logs for one-time links.
- Time-to-access: ensure your zero-trace process is faster than old habits, otherwise users will bypass it.
Preguntas frecuentes
What does zero-trace mean in practice? It means the content is encrypted client side, delivered via a one-time link, and destroyed after access, so there is no readable copy left on the relay or in your communication archive.
Can the recipient still copy or screenshot the secret? Yes, zero-trace removes provider and archive exposure, but the recipient’s device can always copy. Train recipients to store secrets in an approved vault and avoid screenshots.
What if a bot or email gateway opens the link? Many preview systems fetch links automatically. Use providers that support one view with preview-safe delivery, or disable previews on sensitive channels. You can also confirm access with the recipient before burning a second link.
How can we audit access if nothing is stored? Zero-trace services log minimal metadata about an access event, not the content. This gives you accountability, while preserving privacy and minimizing risk.
Are zero-trace links a replacement for password managers? No, they are complementary. Use zero-trace links for transport, then store long lived secrets in a password manager with appropriate access controls.
Is this compatible with GDPR, SOC 2, or ISO 27001 programs? Yes, minimizing retention and separating transport from archives support these programs. For legal advice or certification scope, consult your compliance team.
Comparte información segura con enlaces de cero huella
If your team is still pasting secrets into email or chat, you are carrying unnecessary risk. Make zero-trace your default. Create a self destructing, zero knowledge link in seconds and prove to auditors that you minimized retention by design.
Get started with Nurbak today at nurbak.com.
